- First take the back up of /var/jenkins_home/config.xml or take a snapshot if it’s vm.
Method 1: (all user have same admin access)
- Manage jenkins > Configure Global Security > Active Directory
Domain name : example.com
Domain Controller : ad.exmaple.com
Bind DN : jenkins-svc-account@example.com
Bind Password : <jenkins-svc-account password>

Note: You may need to apply the setting and then click on Test Domain.
Else it will give Error: simple bind failed: ad.example.com:389 error
Also Domain Name(example.com) should be resolved from jenkins host or entry should be in /etc/hosts
192.168.122.6 example.com
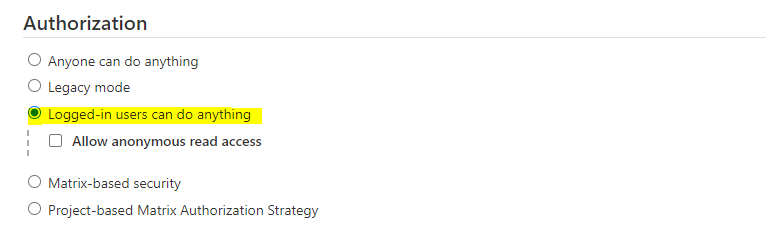
Method 2: Matrix-based security
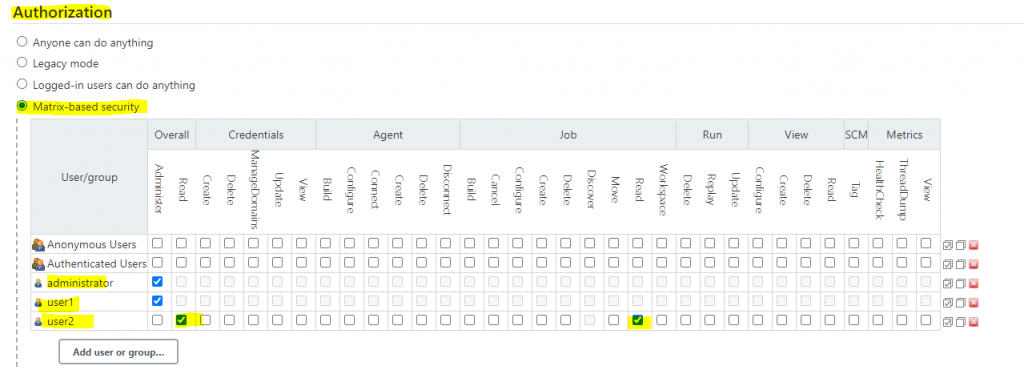
Method3: Role based strategy(pending)
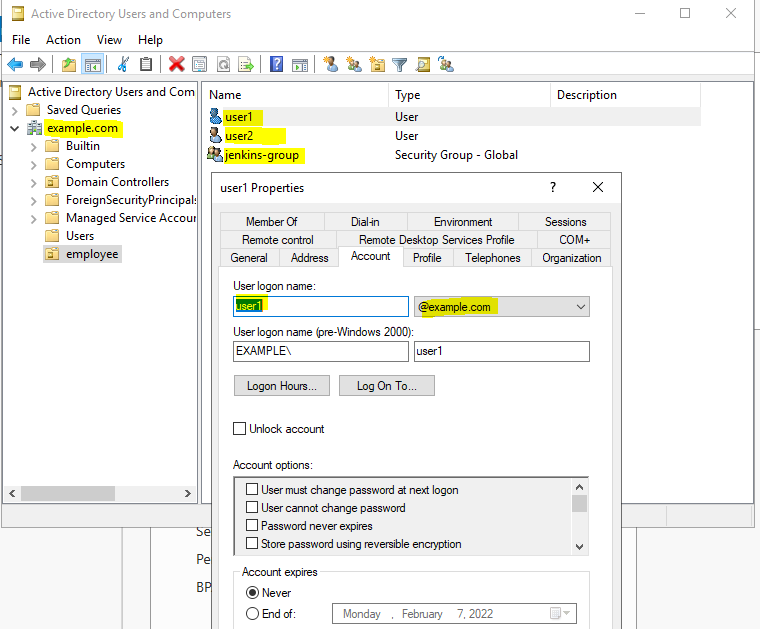
AD user and jenkins screenshot for reference
- Check ldap port in powershell
tnc example.com -port 389
Test-NetConnection -ComputerName example.com -Port 389