CREATE USER 'root'@'%' IDENTIFIED BY 'Test#123';
GRANT ALL PRIVILEGES ON *.* TO 'root'@'%' WITH GRANT OPTION;Month: February 2021
capture TLS/HTTPS traffic via tcpdump
only TLS traffic
tcpdump -ni eth0 "(tcp[((tcp[12] & 0xf0) >> 2)] = 0x16)"
TLS traffic with port
tcpdump -ni eth0 "tcp port 443 and (tcp[((tcp[12] & 0xf0) >> 2)] = 0x16)"
TLS traffic with host ip
tcpdump -ni eth0 "tcp host 10.10.10.10 and (tcp[((tcp[12] & 0xf0) >> 2)] = 0x16)"
Capture packets for wireshark
tcpdump -vvvv -A -i weave '((dst port 80) and (net 10.36.0.15))' -w app2.cap
sudo tcpdump -vvvv -A -i etho -w app2.capMore : https://stackoverflow.com/questions/39624745/capture-only-ssl-handshake-with-tcpdump
https://www.wireshark.org/docs/wsug_html_chunked/AppToolstcpdump.html
Openport using NC:
nc -l 8888Listen port:
nc -l localhost 8888
Send packet using bash:
echo -n "hello" >/dev/tcp/localhost/8888Access sidecar/multi-container pod with kubectl
Get container names in pod:
kubectl describe pod1kubectl exec pod_name1 -c container_name1 -- bash
kubectl exec pod_name1 -c container_name2 -- bash
kunbectl exec --helpmore : https://www.mirantis.com/blog/multi-container-pods-and-container-communication-in-kubernetes/
Jenkins questions list
- install jenkins using docker-compose
- default port for jenkins 8080
- Explain the your CICD pipeline
- What is DSL?
- How do you manage credentials in jenkins?
- explain the basic structure of Jenkinsfile?
- how jobs are managed for different branch/ multibranch?
- What issues you faced in jenkins? = plugin high disk IO
- build trigger?
- how to configure webhook?
- poll SCM?
- light checkout in jekins?
- groovy sandbox?
- add worker node in jenkins? types of method?
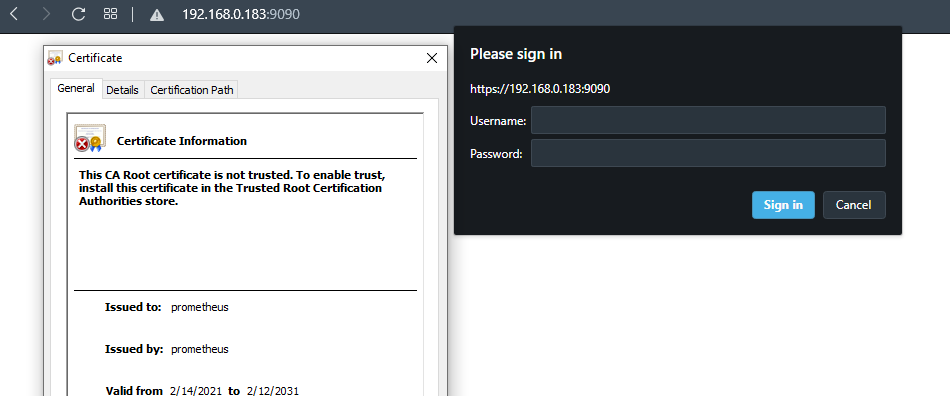
Promethus inbuilt basic authentication and TLS
github : https://github.com/prometheus/prometheus/pull/8316
from v2.24.0 basic authentication and TLS is inbuilt into prometheus.
webconfig.yml
tls_server_config:
cert_file: /etc/prometheus/prometheus.cert
key_file: /etc/prometheus/prometheus.key
basic_auth_users:
admin: $2y$12$/B1Z0Ohq/g9z/BlD30mi/uRDNdBRs/VrtAZrJDtY73Ttjc8RYHJ2O- Start prometheus with webconfig file
./prometheus --web.config.file=webconfig.yml- Prometheus will be accessible on https and with basic auth (admin/admin)
- Password should be bcrypt encrypted – https://bcrypt-generator.com
Disk IO read/write monitor
yum install sysstat -y
iostat -t
iostat -xtc
iostat -d
#More command
iostat -dx /dev/sda 5
sar
vmstat
badblockDocker private registry server
echo '{
"insecure-registries" : [ "192.168.0.183:5000" ]
}' > /etc/docker/daemon.jsondocker run -d -p 5000:5000 --restart=always --name registry registry:2
registry-docker-compose.yml
version: '3'
services:
registry:
image: registry:2
user: root:root
restart: always
container_name: registry
environment:
TZ: "Asia/Kolkata"
volumes:
- /mnt/registry:/var/lib/registry
ports:
- 5000:5000sonarqube stage in jenkins
def git_url = 'https://github.com/initedit/note.initedit'
def git_branch = 'main'
def server_report = "ERROR"
pipeline
{
agent
{
label 'master'
}
stages
{
stage('Git Checkout')
{
steps
{
git credentialsId: 'github', url: git_url , branch: git_branch
}
}
stage('sonarqube analysis')
{
steps
{
script
{
withSonarQubeEnv('sonarqube')
{
def temp_job_name = JOB_NAME.replaceAll('/','-')
sh "PATH=$PATH:/var/jenkins_home/node12/bin;NODE_PATH=/var/jenkins_home/node12/lib/node_modules;npm install typescript;/var/jenkins_home/sonar_scanner/bin/sonar-scanner -Dsonar.sourceEncoding=UTF-8 -Dsonar.sources=${WORKSPACE} -Dsonar.projectKey=${temp_job_name}-${git_branch} -Dsonar.projectName=${temp_job_name}-${git_branch};"
withCredentials([usernamePassword(credentialsId: 'sonarqube-user', usernameVariable: 'uname' , passwordVariable: 'upass')])
{
sh """
cd .scannerwork
sonar_job_url=\$(cat report-task.txt | grep ceTaskUrl | awk -F 'ceTaskUrl=' '{print \$NF}')
while(true)
do
sonar_job_status=\$(curl -s --user "\$uname:\$upass" \$sonar_job_url | awk -F '"status":' '{print \$NF}' | cut -d ',' -f1 | sed 's/"//g')
sleep 10
if [ "\$sonar_job_status" != 'IN_PROGRESS' ]
then
echo "sonar job completed"
#get new bugs
new_vulnerabilities=\$(curl -s --user "\$uname:\$upass" http://sonarqube.initedit.com/api/measures/search_history?component="${temp_job_name}-${git_branch}"'&'metrics=new_vulnerabilities | awk -F '"value":' '{print \$NF}' | awk -F '}' '{print \$1}' | sed 's/"//g')
new_bugs=\$(curl -s --user "\$uname:\$upass" http://sonarqube.initedit.com/api/measures/search_history?component="${temp_job_name}-${git_branch}"'&'metrics=new_bugs | awk -F '"value":' '{print \$NF}' | awk -F '}' '{print \$1}' | sed 's/"//g')
new_violations=\$(curl -s --user "\$uname:\$upass" http://sonarqube.initedit.com/api/measures/search_history?component="${temp_job_name}-${git_branch}"'&'metrics=new_violations | awk -F '"value":' '{print \$NF}' | awk -F '}' '{print \$1}' | sed 's/"//g')
echo "new_vulnerabilities=\$new_vulnerabilities new_bugs=\$new_bugs new_violations=\$new_violations" > /tmp/\${JOB_BASE_NAME}-\${BUILD_ID}.txt
cat "/tmp/\${JOB_BASE_NAME}-\${BUILD_ID}.txt"
echo "new_vulnerabilities: \$new_vulnerabilities , new_bugs : \$new_bugs , new_violations : \$new_violations"
exit
fi
done
"""
}
}
def qualitygate = waitForQualityGate()
server_report = qualitygate.status
}
}
}
stage('sonar-qualitygate')
{
steps
{
script
{
if (server_report != 'OK')
{
sh '''
echo "not ok"
'''
}
}
}
}
}
}101 questions list for troubleshooting issues
- What error message your are getting? screenshot?
- What actual issue you are facing share your screen?
- What your are trying to accomplish?
- When did it last work? approx. timing?
- Is everyone in your team having the same issue?
- What is the endpoint? Port? URL? IPaddress?
- is this the first time you are accessing this URL?