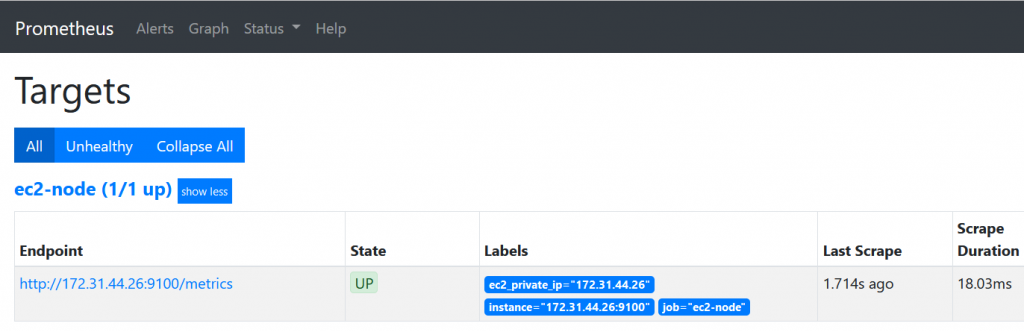
- Create role(
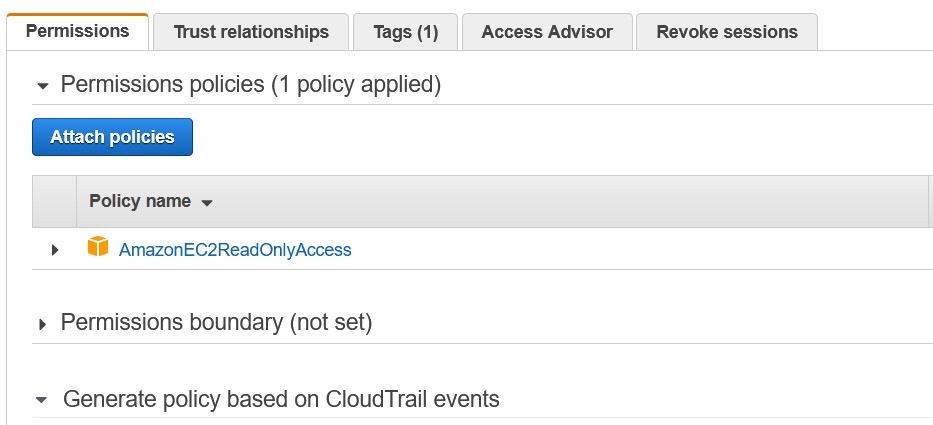
prometheus-ec2) withAmazonEC2ReadOnlyAccesspolicy - Attach role to ec2
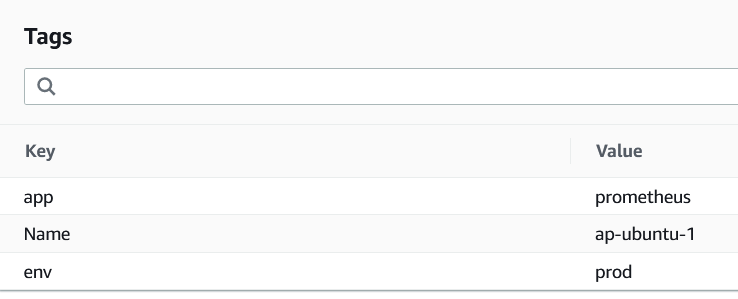
- Tag ec2
prometheus.yml
kind: ConfigMap
apiVersion: v1
metadata:
name: prometheus-conf
data:
prometheus.yml: |
global:
scrape_interval: 10s
evaluation_interval: 10s
scrape_configs:
- job_name: 'ec2-node'
ec2_sd_configs:
- region: ap-south-1
port: 9100
relabel_configs:
- source_labels: [__meta_ec2_tag_app]
action: keep
regex: 'pro.*'
- source_labels: [__meta_ec2_private_ip]
action: replace
target_label: ec2_private_ip