only TLS traffic
tcpdump -ni eth0 "(tcp[((tcp[12] & 0xf0) >> 2)] = 0x16)"
TLS traffic with port
tcpdump -ni eth0 "tcp port 443 and (tcp[((tcp[12] & 0xf0) >> 2)] = 0x16)"
TLS traffic with host ip
tcpdump -ni eth0 "tcp host 10.10.10.10 and (tcp[((tcp[12] & 0xf0) >> 2)] = 0x16)"
Capture packets for wireshark
tcpdump -vvvv -A -i weave '((dst port 80) and (net 10.36.0.15))' -w app2.cap
sudo tcpdump -vvvv -A -i etho -w app2.capMore : https://stackoverflow.com/questions/39624745/capture-only-ssl-handshake-with-tcpdump
https://www.wireshark.org/docs/wsug_html_chunked/AppToolstcpdump.html
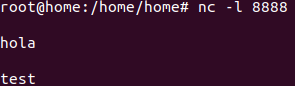
Openport using NC:
nc -l 8888Listen port:
nc -l localhost 8888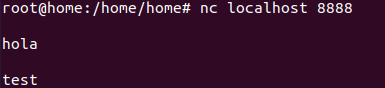
Send packet using bash:
echo -n "hello" >/dev/tcp/localhost/8888