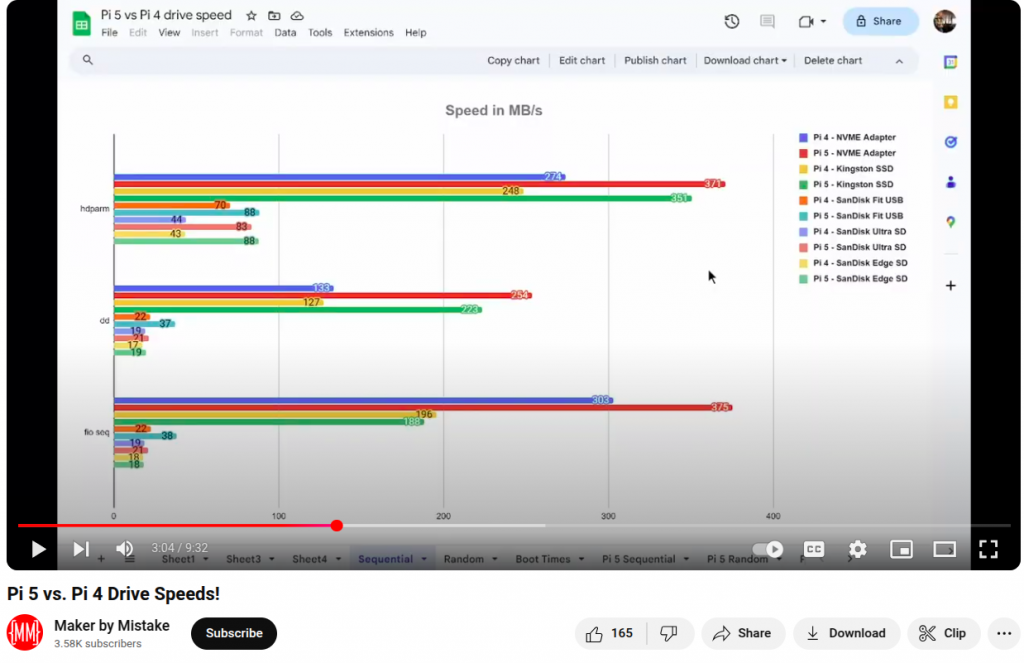
sudo curl https://raw.githubusercontent.com/TheRemote/PiBenchmarks/master/Storage.sh | sudo bashroot@lp-arm-1:~# mmc cid read /sys/block/mmcblk0/device
type: 'SD'
manufacturer: 'Unlisted' 'SC'
product: 'EC1S5' 3.0
root@lp-arm-1:~#
Category Test Result
HDParm Disk Read 41.53 MB/sec
HDParm Cached Disk Read 41.88 MB/sec
DD Disk Write 11.3 MB/s
FIO 4k random read 3646 IOPS (14586 KB/s)
FIO 4k random write 620 IOPS (2481 KB/s)
IOZone 4k read 8160 KB/s
IOZone 4k write 1897 KB/s
IOZone 4k random read 6715 KB/s
IOZone 4k random write 2006 KB/s
Score: 893
==========================================================
root@lp-arm-2:~# mmc cid read /sys/block/mmcblk0/device
type: 'SD'
manufacturer: 'SanDisk' 'SD'
product: 'SD32G' 8.5
root@lp-arm-2:~#
Category Test Result
HDParm Disk Read 38.89 MB/sec
HDParm Cached Disk Read 37.33 MB/sec
DD Disk Write 18.3 MB/s
FIO 4k random read 2692 IOPS (10771 KB/s)
FIO 4k random write 926 IOPS (3706 KB/s)
IOZone 4k read 7577 KB/s
IOZone 4k write 1803 KB/s
IOZone 4k random read 6164 KB/s
IOZone 4k random write 3204 KB/s
Score: 1048
==========================================================
root@lp-arm-3:~# lshw -class disk
*-disk
description: SCSI Disk
product: Storage Device
vendor: Mass
physical id: 0.0.0
bus info: scsi@0:0.0.0
logical name: /dev/sda
size: 447GiB (480GB)
root@lp-arm-3:~#
Category Test Result
HDParm Disk Read 31.01 MB/sec
HDParm Cached Disk Read 29.69 MB/sec
DD Disk Write 27.4 MB/s
FIO 4k random read 512 IOPS (2048 KB/s)
FIO 4k random write 2871 IOPS (11484 KB/s)
IOZone 4k read 12668 KB/s
IOZone 4k write 10282 KB/s
IOZone 4k random read 10202 KB/s
IOZone 4k random write 11744 KB/s
Score: 2400
=================================================
root@lp-arm-4:~# mmc cid read /sys/block/mmcblk0/device
type: 'SD'
manufacturer: 'SanDisk' 'SD'
product: 'SD32G' 8.5
root@lp-arm-4:~#
Category Test Result
HDParm Disk Read 39.28 MB/sec
HDParm Cached Disk Read 35.07 MB/sec
DD Disk Write 17.4 MB/s
FIO 4k random read 2967 IOPS (11869 KB/s)
FIO 4k random write 876 IOPS (3506 KB/s)
IOZone 4k read 7180 KB/s
IOZone 4k write 1844 KB/s
IOZone 4k random read 5824 KB/s
IOZone 4k random write 2350 KB/s
Score: 942
==================================================
root@pi5:~# mmc cid read /sys/block/mmcblk0/device
type: 'SD'
manufacturer: 'Transcend/Samsung' 'SM'
product: 'ED2S5' 3.0
root@pi5:~#
Category Test Result
HDParm Disk Read 42.00 MB/sec
HDParm Cached Disk Read 80.31 MB/sec
DD Disk Write 54.6 MB/s
FIO 4k random read 4227 IOPS (16911 KB/s)
FIO 4k random write 833 IOPS (3333 KB/s)
IOZone 4k read 21831 KB/s
IOZone 4k write 3226 KB/s
IOZone 4k random read 16273 KB/s
IOZone 4k random write 3229 KB/s
Score: 2035
- DD command with 1GB
root@pi5:~# dd if=/dev/zero of=/tmp/test1.img bs=1G count=1 oflag=dsync
1+0 records in
1+0 records out
1073741824 bytes (1.1 GB, 1.0 GiB) copied, 20.0689 s, 53.5 MB/s
root@lp-arm-1:~# dd if=/dev/zero of=/tmp/test1.img bs=1G count=1 oflag=dsync
1+0 records in
1+0 records out
1073741824 bytes (1.1 GB, 1.0 GiB) copied, 117.843 s, 9.1 MB/s
root@lp-arm-2:~# dd if=/dev/zero of=/tmp/test1.img bs=1G count=1 oflag=dsync
1+0 records in
1+0 records out
1073741824 bytes (1.1 GB, 1.0 GiB) copied, 72.3963 s, 14.8 MB/s
###########pi4 with old USB-to-SATA cable###########
root@lp-arm-3:~# dd if=/dev/zero of=/tmp/test1.img bs=1G count=1 oflag=dsync
1+0 records in
1+0 records out
1073741824 bytes (1.1 GB, 1.0 GiB) copied, 39.0338 s, 27.5 MB/s
###########pi4 with new USB-to-SATA cable###########
pi@lp-arm-3:~ $ dd if=/dev/zero of=/tmp/test2.img bs=1G count=1 oflag=dsync
1+0 records in
1+0 records out
1073741824 bytes (1.1 GB, 1.0 GiB) copied, 5.6486 s, 190 MB/s
#######################################################
root@lp-arm-4:~# dd if=/dev/zero of=/tmp/test1.img bs=1G count=1 oflag=dsync
1+0 records in
1+0 records out
1073741824 bytes (1.1 GB, 1.0 GiB) copied, 183.551 s, 5.8 MB/s
[root@lp-k8control-1 ~]# dd if=/dev/zero of=/tmp/test1.img bs=1G count=1 oflag=dsync
1+0 records in
1+0 records out
1073741824 bytes (1.1 GB, 1.0 GiB) copied, 11.1345 s, 96.4 MB/s
[root@lp-knode-1 ~]# dd if=/dev/zero of=/tmp/test1.img bs=1G count=1 oflag=dsync
1+0 records in
1+0 records out
1073741824 bytes (1.1 GB, 1.0 GiB) copied, 9.51946 s, 113 MB/s
root@lp-proxmox-1:~# dd if=/dev/zero of=/tmp/test1.img bs=1G count=1 oflag=dsync
1+0 records in
1+0 records out
1073741824 bytes (1.1 GB, 1.0 GiB) copied, 8.93593 s, 120 MB/s
home@home:~$ dd if=/dev/zero of=/tmp/test1.img bs=1G count=1 oflag=dsync
1+0 records in
1+0 records out
1073741824 bytes (1.1 GB, 1.0 GiB) copied, 1.69814 s, 632 MB/s
========Crucial 1000GB SSD with SATA USB 3.0 with laptop=====
home@home:~$ dd if=/dev/zero of=/media/home/backup-ssd1/test1.img bs=1G count=1 oflag=dsync
1+0 records in
1+0 records out
1073741824 bytes (1.1 GB, 1.0 GiB) copied, 3.08829 s, 348 MB/s
========Crucial 1000GB SSD with SATA USB 3.0 with pi5 ntfs=====
root@pi5:~# dd if=/dev/zero of=/media/home/backup-ssd1/test1.img bs=1G count=1 oflag=dsync
1+0 records in
1+0 records out
1073741824 bytes (1.1 GB, 1.0 GiB) copied, 4.16956 s, 258 MB/s
===========pi5===Sandisk-extreme=======================
root@pi5-sandisk:/home/pi# dd if=/dev/zero of=/tmp/test1.img bs=1G count=1 oflag=dsync
1+0 records in
1+0 records out
1073741824 bytes (1.1 GB, 1.0 GiB) copied, 15.1769 s, 70.7 MB/s
===========pi5===Samsung evo plus=======================
root@lp-arm-1:~# dd if=/dev/zero of=/tmp/test1.img bs=1G count=1 oflag=dsync
1+0 records in
1+0 records out
1073741824 bytes (1.1 GB, 1.0 GiB) copied, 20.0689 s, 53.5 MB/s
===========pi4===Sandisk-extreme=======================
root@lp-arm-4:~# dd if=/dev/zero of=/tmp/test1.img bs=1G count=1 oflag=dsync
1+0 records in
1+0 records out
1073741824 bytes (1.1 GB, 1.0 GiB) copied, 28.8803 s, 37.2 MB/s
===========pi4===Samsung evo plus=======================
root@lp-arm-1:~# dd if=/dev/zero of=/tmp/test1.img bs=1G count=1 oflag=dsync
1+0 records in
1+0 records out
1073741824 bytes (1.1 GB, 1.0 GiB) copied, 30.305 s, 35.4 MB/s
============on pi4 NFS server 188============================
root@lp-knode-2:~# dd if=/dev/zero of=/mnt/nfs188/test1.img bs=1G count=1 oflag=dsync
1+0 records in
1+0 records out
1073741824 bytes (1.1 GB, 1.0 GiB) copied, 11.2499 s, 95.4 MB/s
################ Ansible speed check(4-7-2025)##############
ok: [lp-knode-1.home] => {
"msg": "1+0 records in\n1+0 records out\n1073741824 bytes (1.1 GB, 1.0 GiB) copied, 6.88063 s, 156 MB/s"
}
ok: [lp-knode-2.home] => {
"msg": "1+0 records in\n1+0 records out\n1073741824 bytes (1.1 GB, 1.0 GiB) copied, 1.58189 s, 679 MB/s"
}
ok: [lp-arm-1.home] => {
"msg": "1+0 records in\n1+0 records out\n1073741824 bytes (1.1 GB, 1.0 GiB) copied, 39.8816 s, 26.9 MB/s"
}
ok: [lp-arm-2.home] => {
"msg": "1+0 records in\n1+0 records out\n1073741824 bytes (1.1 GB, 1.0 GiB) copied, 60.2801 s, 17.8 MB/s"
}
ok: [lp-arm-4.home] => {
"msg": "1+0 records in\n1+0 records out\n1073741824 bytes (1.1 GB, 1.0 GiB) copied, 29.3403 s, 36.6 MB/s"
}
More test ref: