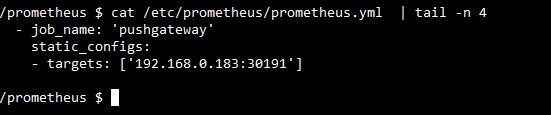
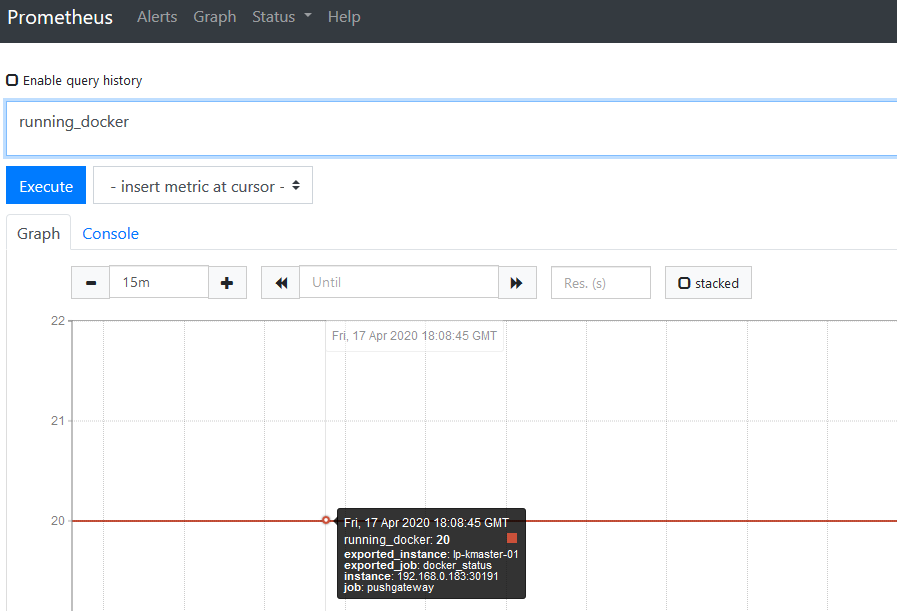
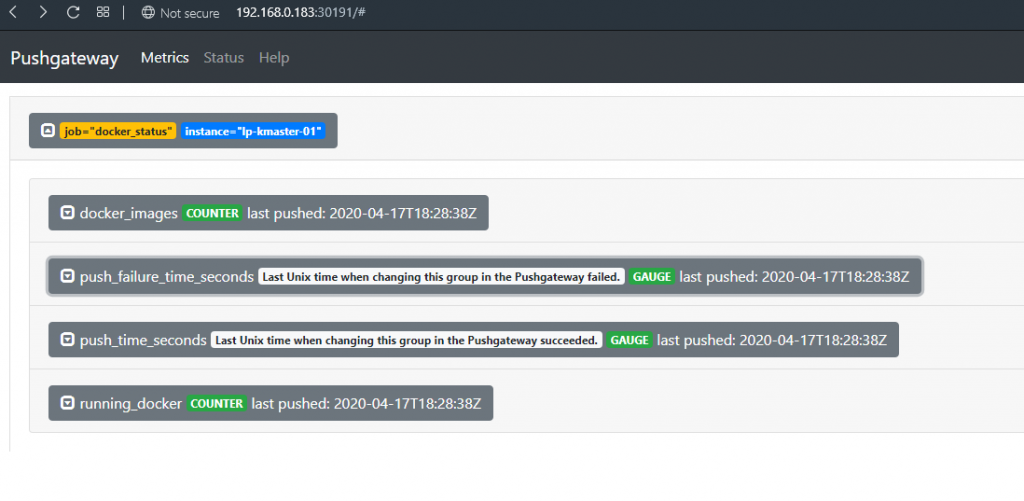
Note:
– for sonarqube 8 set sysctl -w vm.max_map_count=262144 on host machine
– Move all extensions jars from container to your extensions dir
1.postgress.yml
apiVersion: apps/v1
kind: Deployment
metadata:
name: postgres-deployment
labels:
app: postgres
env: prod
spec:
replicas: 1
selector:
matchLabels:
app: postgres
env: prod
template:
metadata:
labels:
app: postgres
env: prod
spec:
containers:
- name: postgres-container
image: postgres
imagePullPolicy: IfNotPresent
resources:
requests:
memory: "256Mi"
cpu: "100m"
limits:
memory: "512Mi"
cpu: "200m"
env:
- name: POSTGRES_PASSWORD
value: "PASSWORD"
volumeMounts:
- name: postgres-data
mountPath: /var/lib/postgresql/data
ports:
- containerPort: 5432
volumes:
- name: postgres-data
nfs:
server: 192.168.0.184
path: "/opt/nfs1/postgres/data"
---
kind: Service
apiVersion: v1
metadata:
name: postgres-service
labels:
app: postgres
env: prod
spec:
selector:
app: postgres
env: prod
ports:
- name: postgres
protocol: TCP
port: 5432
targetPort: 5432
nodePort: 30432
type: NodePort2.sonarqube.yml
apiVersion: apps/v1
kind: Deployment
metadata:
name: sonarqube-deployment
labels:
app: sonarqube
env: prod
spec:
replicas: 1
selector:
matchLabels:
app: sonarqube
env: prod
template:
metadata:
labels:
app: sonarqube
env: prod
spec:
containers:
- name: sonarqube-container
image: sonarqube:7.7-community
imagePullPolicy: IfNotPresent
env:
- name: SONARQUBE_JDBC_USERNAME
value: postgres
- name: SONARQUBE_JDBC_PASSWORD
value: "PASSWORD"
- name: SONARQUBE_JDBC_URL
value: jdbc:postgresql://postgres-service:5432/sonar
resources:
requests:
memory: "1024Mi"
cpu: "500m"
limits:
memory: "2048Mi"
cpu: "1000m"
volumeMounts:
- name: sonarqube-conf
mountPath: /opt/sonarqube/conf
- name: sonarqube-data
mountPath: /opt/sonarqube/data
- name: sonarqube-logs
mountPath: /opt/sonarqube/logs
- name: sonarqube-extensions
mountPath: /opt/sonarqube/extensions
ports:
- containerPort: 9000
volumes:
- name: sonarqube-conf
nfs:
server: 192.168.0.184
path: "/opt/nfs1/sonarqube/conf"
- name: sonarqube-data
nfs:
server: 192.168.0.184
path: "/opt/nfs1/sonarqube/data"
- name: sonarqube-logs
nfs:
server: 192.168.0.184
path: "/opt/nfs1/sonarqube/logs"
- name: sonarqube-extensions
nfs:
server: 192.168.0.184
path: "/opt/nfs1/sonarqube/extensions"
---
kind: Service
apiVersion: v1
metadata:
name: sonarqube-service
labels:
app: sonarqube
env: prod
spec:
selector:
app: sonarqube
env: prod
ports:
- name: sonarqube
protocol: TCP
port: 9000
targetPort: 9000
nodePort: 30900
type: NodePortNote: Create sonar database in postgres
https://stackoverflow.com/questions/16825331/disallow-anonymous-users-to-access-sonar