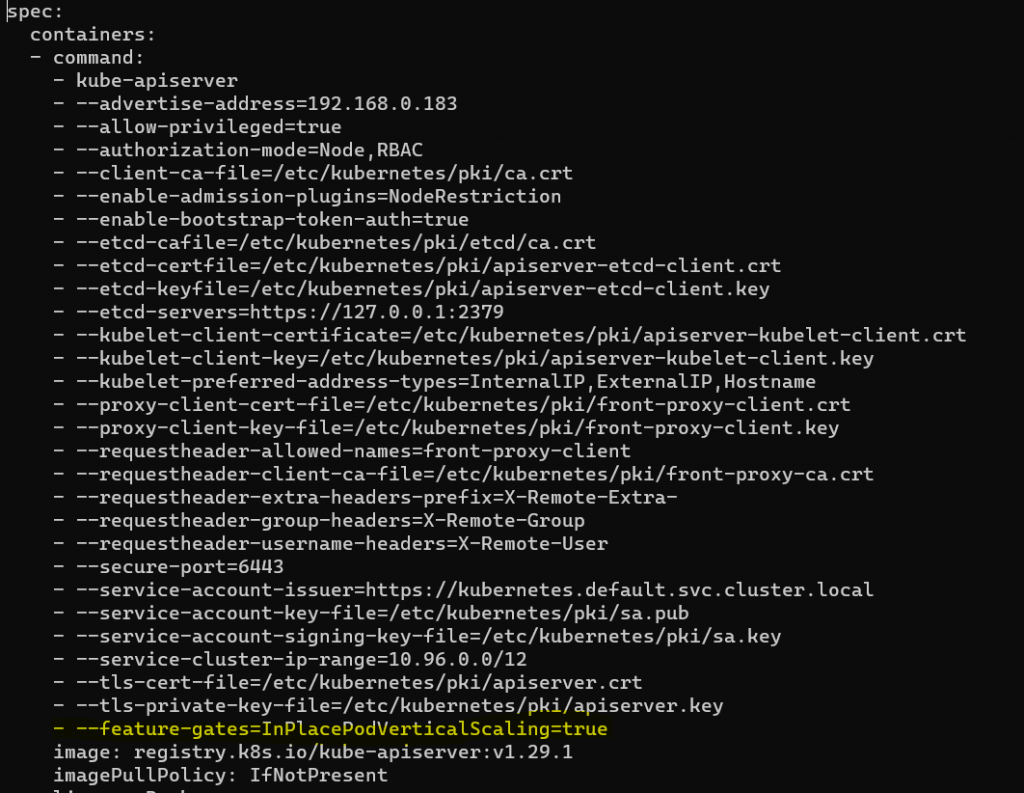
kubectl custom query to get cpu , memory request and limit
kubectl get deploy -A -o=custom-columns='Namespace:.metadata.namespace,Name:.metadata.name,Request_CPU:.spec.template.spec.containers[0].resources.requests.cpu,Limit_CPU:.spec.template.spec.containers[0].resources.limits.cpu,Request_Memory:.spec.template.spec.containers[0].resources.requests.memory,Limit_Memory:.spec.template.spec.containers[0].resources.limits.memory' | sed 1d | tr -s '[:blank:]' ','kubect replace variabe
deployments=$(kubectl get deploy | awk '{print $1}' | sed 1d)
for deploy in $deployments
do
deploy_raw_yml=$(kubectl get deploy $deploy -o yaml)
kubectl get deploy $deploy -o yaml > _tmp_store.yml
value_to_be_replaced=$(kubectl get deploy $deploy -o yaml | grep -A 1 'NEW_RELIC_APP_NAME' | grep value | awk -F 'value: ' '{print $2}')
echo "value_to_be_replaced: $value_to_be_replaced"
if [[ $value_to_be_replaced == "" ]]; then
echo "=====================$deploy no change =========================="
else
replaced_value=$(echo $value_to_be_replaced | sed 's/stage/perf/g')
echo "replaced_value: $replaced_value"
cat _tmp_store.yml| sed "s/$value_to_be_replaced/$replaced_value/g" | kubectl apply -f -
echo "=====================$deploy done =========================="
fi
done