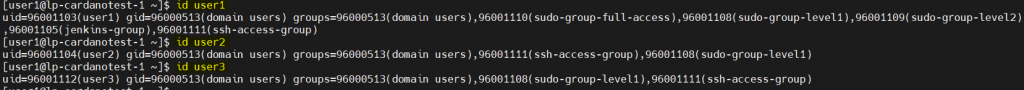
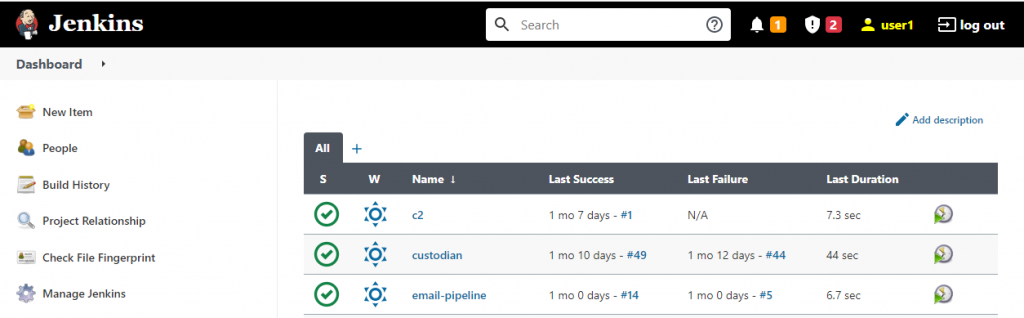
- zip-password-finder : https://github.com/agourlay/zip-password-finder
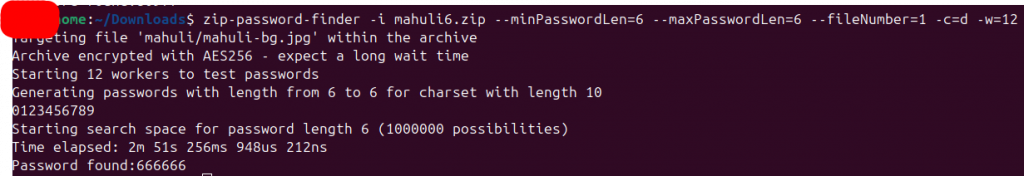
@home:~/Downloads$ zip-password-finder -i mahuli6.zip --minPasswordLen=6 --maxPasswordLen=6 --fileNumber=1 -c=d -w=12
Targeting file 'mahuli/mahuli-bg.jpg' within the archive
Archive encrypted with AES256 - expect a long wait time
Starting 12 workers to test passwords
Generating passwords with length from 6 to 6 for charset with length 10
0123456789
Starting search space for password length 6 (1000000 possibilities)
Time elapsed: 2m 51s 256ms 948us 212ns
Password found:666666
unshadow /etc/passwd /etc/shadow > pass.txt
user@home:~$ john pass.txt
user@home:~$ john pass.txt --show
abc1:11111111:1000:1000:abc1:/home/abc1:/bin/bash
abc2:22222222:1002:1002:,,,:/home/abc2:/bin/bash
user@home:~$ ls .john/
john.log john.potNote: Don’t use simple password.