- Run Keycloak with docker-compose
version: '3'
services:
postgres:
image: postgres:9.6
volumes:
- /opt/postgres/:/var/lib/postgresql/data
environment:
POSTGRES_DB: keycloak_db
POSTGRES_USER: keycloak_user
POSTGRES_PASSWORD: password
keycloak:
image: quay.io/keycloak/keycloak:latest
environment:
DB_VENDOR: POSTGRES
DB_ADDR: postgres
DB_DATABASE: keycloak_db
DB_USER: keycloak_user
DB_SCHEMA: public
DB_PASSWORD: password
KEYCLOAK_USER: admin
KEYCLOAK_PASSWORD: admin
ports:
- 8080:8080
depends_on:
- postgres
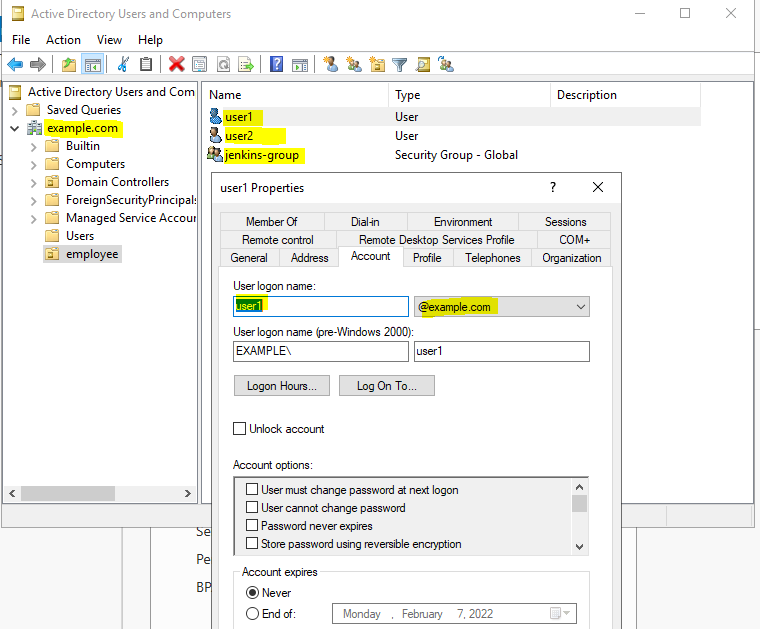
- Open Keycloak panel : http://192.168.0.184:8080 > add realm > Jenkins
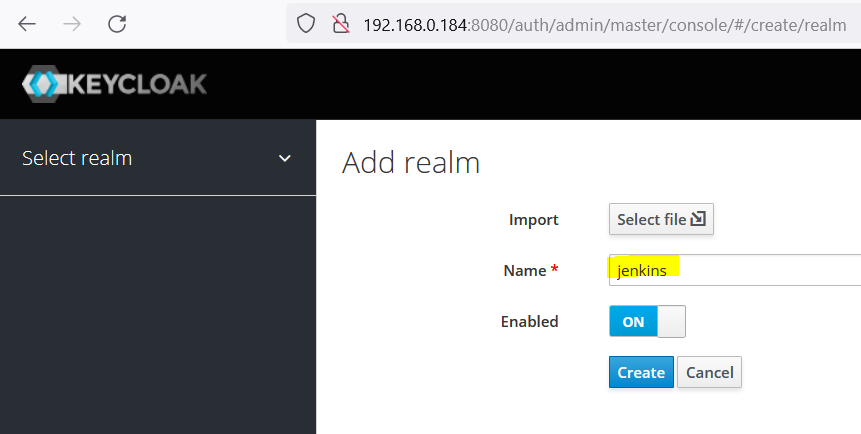
- Add client, Client > client-protocal=openid-connect > Root URL
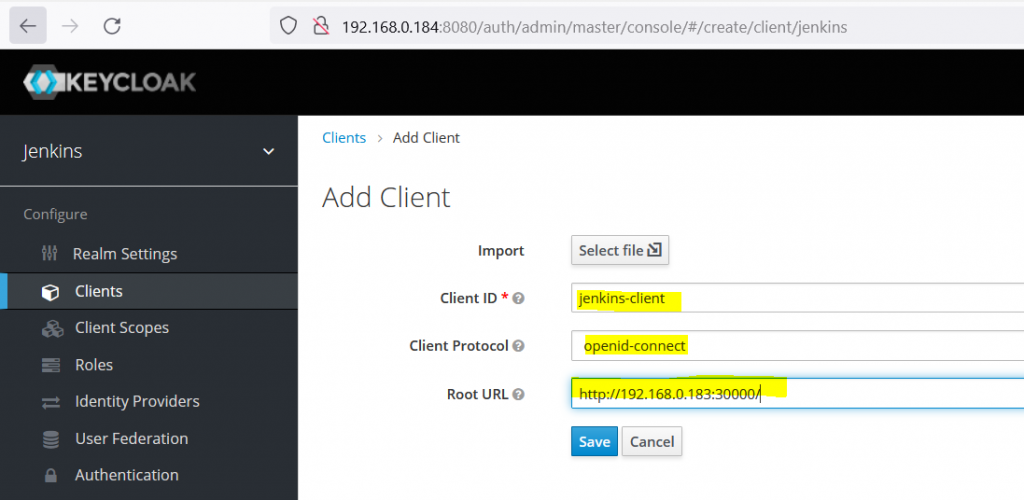
- Client > Jenkins-client > Installation > Keycloak OIDC JSON > Download
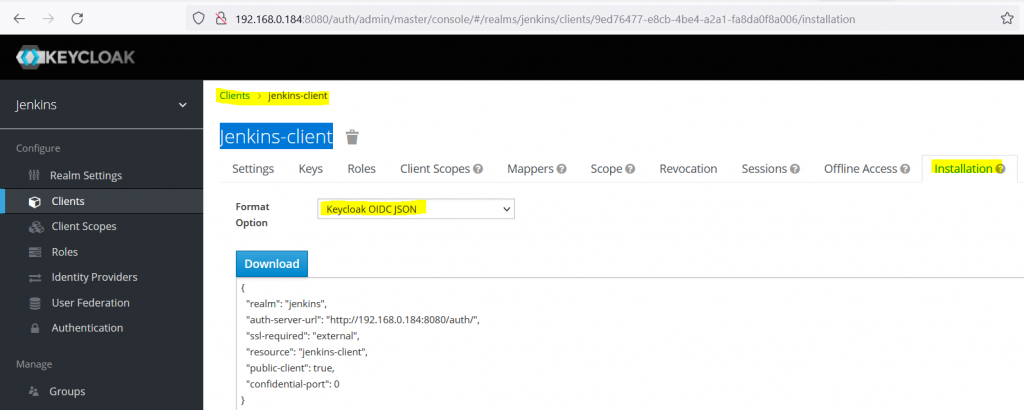
Note : Take the back up of /var/jenkins_home/config.xml or take a snapshot if it’s vm.
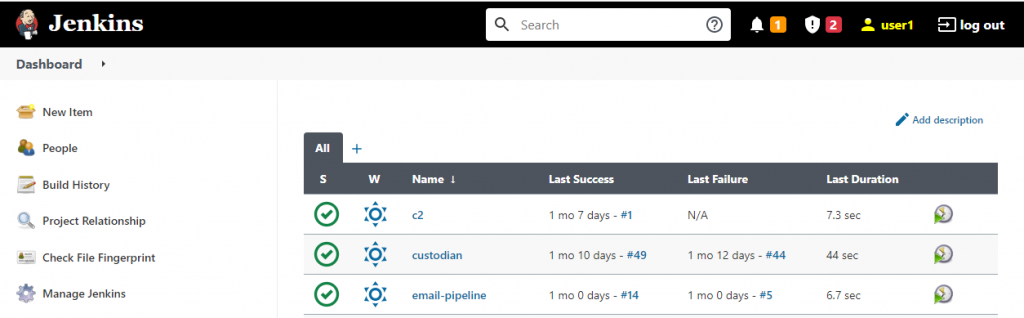
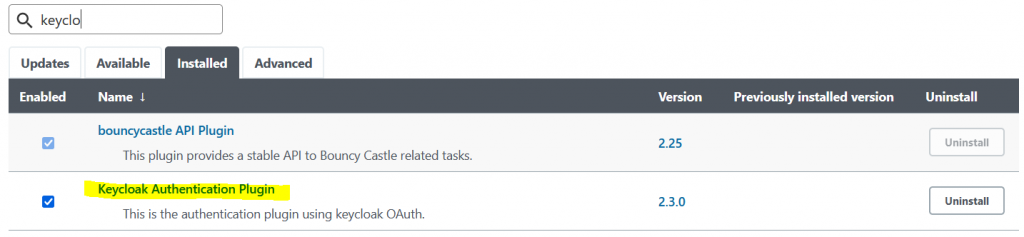
- Login to Jenkins > Manage jenkins > Manage plugins > Install Keycloak Authentication Plugin
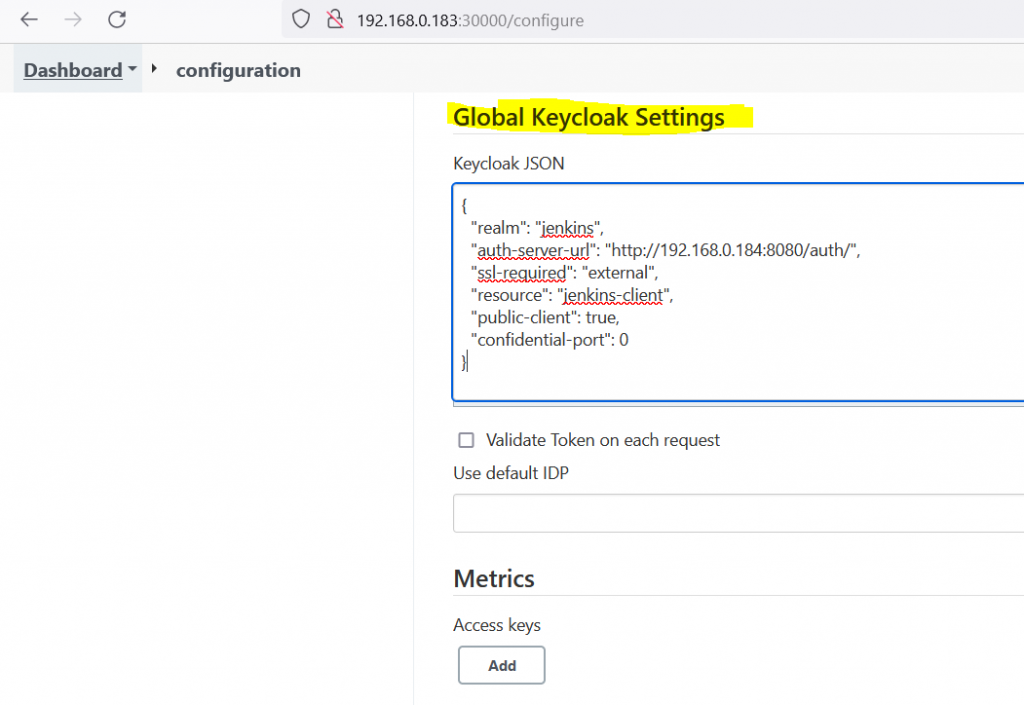
- Manage Jenkins > Configure system > Global Keycloak Settings > add downloaded json data > Save
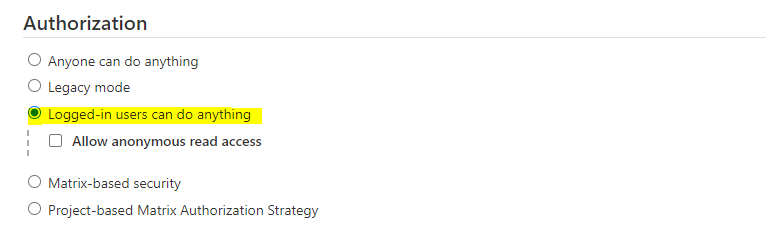
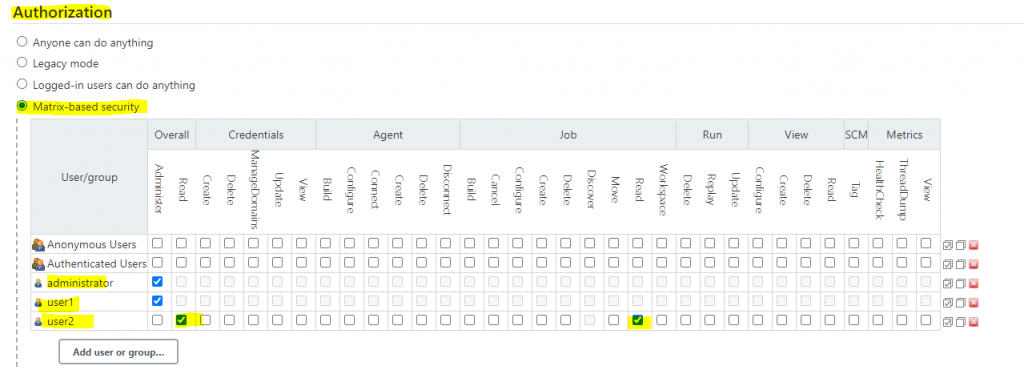
- Manage Jenkins > Configure global security > Securiy Realm > Keycloak Authentication Plugin > Save and logout
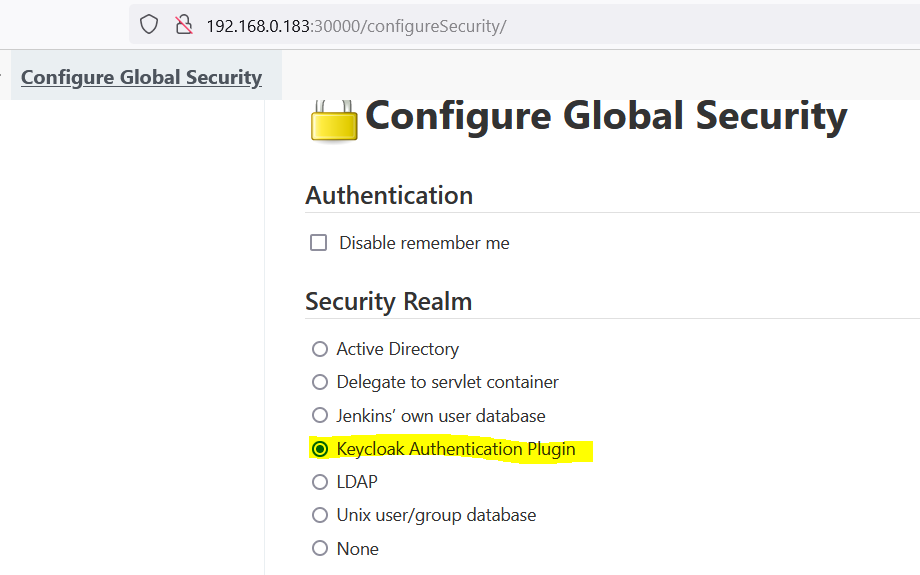
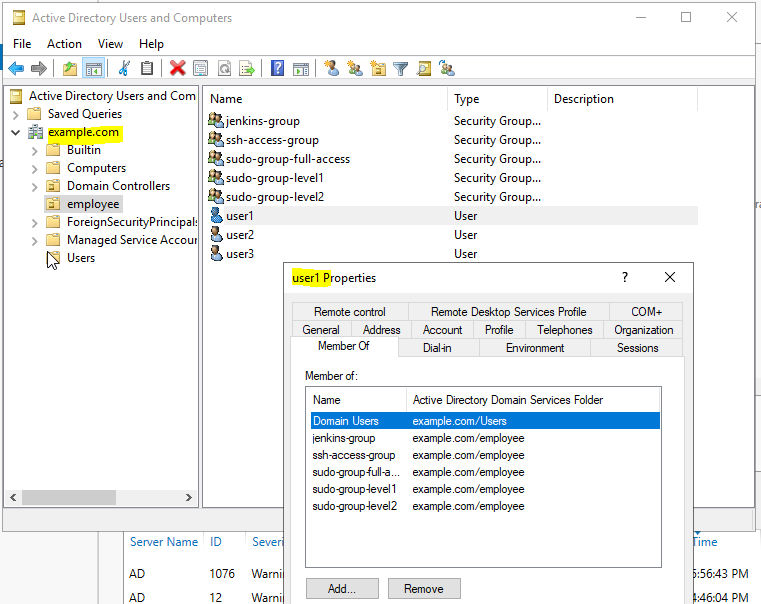
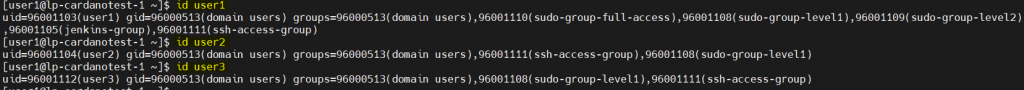
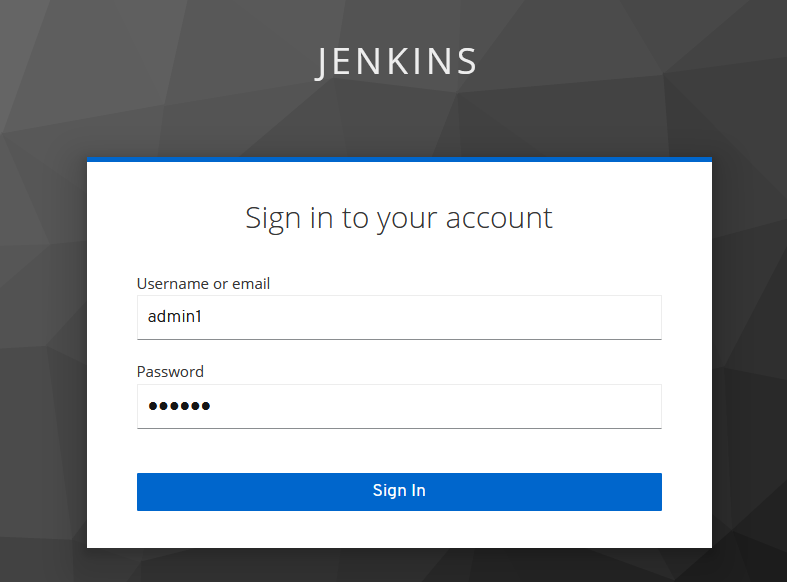
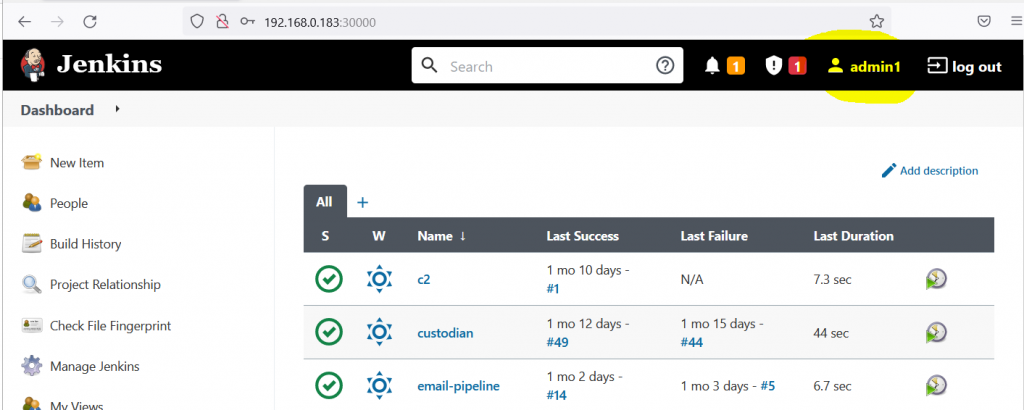
- Create Users in Keycloak realm “jenkins” and login with user(eg. admin1)
More – https://www.keycloak.org/getting-started/getting-started-docker