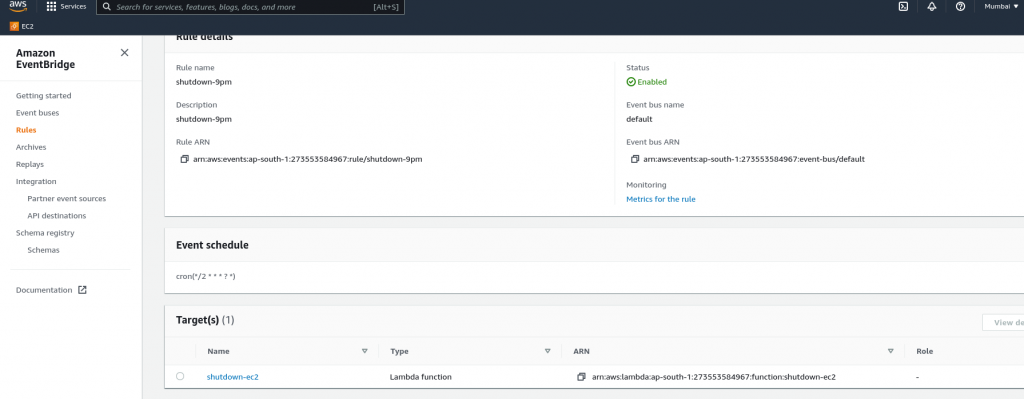
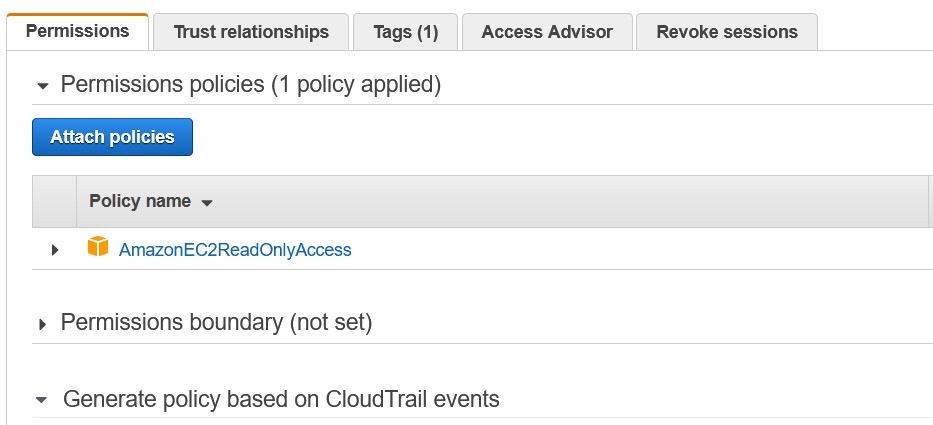
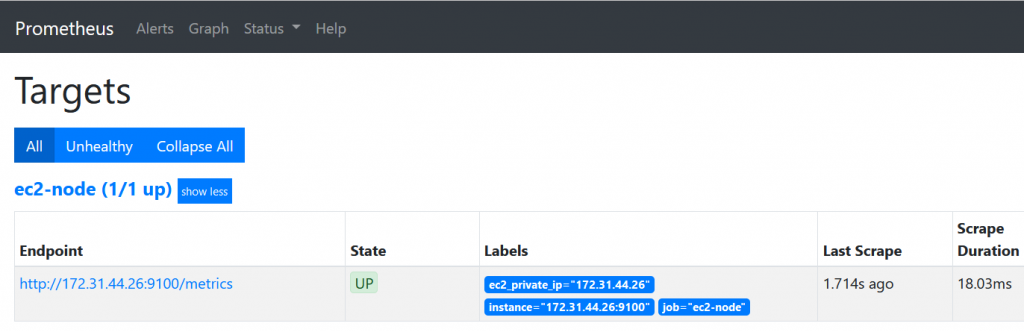
Note : If we creates eks cluster from UI it’s creates with different user and gives error when we do kubectl get pod
aws eks get-token --cluster-name eks1
aws eks update-kubeconfig --name eks1
aws sts get-caller-identity
aws sts assume-role --role-arn "arn:aws:iam::1111111111:role/role-name" --role-session-name "tests3"
aws --profile=default eks update-kubeconfig --name eks1
aws eks create-cluster \
--region ap-south-1 \
--name eks1 \
--kubernetes-version 1.20 \
--role-arn arn:aws:iam::account_number:role/eks1-clst \
--resources-vpc-config subnetIds=subnet-093a2ddfcb7bc30b1,subnet-0475d9e26dfdc9d00,subnet-0274975b4af3513ee
aws eks describe-cluster \
--region ap-south-1 \
--name eks1 \
--query "cluster.status"
https://docs.aws.amazon.com/eks/latest/userguide/create-cluster.html
always check the minimum version of aws cli for eks
https://stackoverflow.com/questions/50791303/kubectl-error-you-must-be-logged-in-to-the-server-unauthorized-when-accessing
https://aws.amazon.com/premiumsupport/knowledge-center/eks-api-server-unauthorized-error/