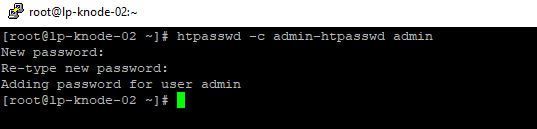
if grafana is running on https and you do not add below setting it will give HTTP ERROR 400
nginx.ingress.kubernetes.io/backend-protocol: "HTTPS"- Also check
grafana.iniaurdefault.inifor root_url
root_url = https://grafana.example.com- Also check the liveness and readiness probe scheme
- grafana helm values.yaml
image:
repository: grafana/grafana
tag: 8.5.2
persistence:
enabled: true
type: statefulset
resources:
limits:
cpu: 500m
memory: 512Mi
requests:
cpu: 500m
memory: 512Mi
grafana.ini:
app_mode: test
paths:
data: /var/lib/grafana/
logs: /var/log/grafana
plugins: /var/lib/grafana/plugins
provisioning: /etc/grafana/provisioning
temp_data_lifetime: 24h
server:
protocol: https
domain: grafana.example.com
enforce_domain: false
root_url: https://grafana.example.com/
serve_from_sub_path: false
cert_file: /var/lib/grafana/cert/dev.crt
cert_key: /var/lib/grafana/cert/dev.key
database:
type: postgres
host: database-hostname
name: grafana
user: grafana
password: ${grafana_eks_postgres_password}
ssl_mode: disable
security:
cookie_secure: true
allow_embedding: true
strict_transport_security: true
strict_transport_security_max_age_seconds: 31536000
strict_transport_security_preload: true
strict_transport_security_subdomains: true
x_content_type_options: true
x_xss_protection: true
smtp:
enabled: true
host: email-smtp.ap-south-1.amazonaws.com:25
user: ${grafana_smtp_username}
password: ${grafana_smtp_password}
#skip_verify = true
from_address: exam@example.com
from_name: test
readinessProbe:
httpGet:
path: /api/health
port: 3000
scheme: HTTPS
livenessProbe:
httpGet:
path: /api/health
port: 3000
scheme: HTTPS
initialDelaySeconds: 60
timeoutSeconds: 30
failureThreshold: 10
ingress:
enabled: true
annotations:
kubernetes.io/ingress.class: nginx
nginx.ingress.kubernetes.io/proxy-connect-timeout: "600"
nginx.ingress.kubernetes.io/proxy-read-timeout: "600"
nginx.ingress.kubernetes.io/proxy-send-timeout: "600"
route53mapper: enabled
nginx.ingress.kubernetes.io/backend-protocol: HTTPS
labels:
app: grafana
path: /
pathType: ImplementationSpecific
hosts:
- grafana.example.comhelm upgrade --install grafana grafana/grafana --version 6.32.6 --set image.tag=8.5.2 --set persistence.enabled=true --set persistence.type=statefulset --set persistence.storageClassName=gp2
helm upgrade --install grafana grafana/grafana --version 6.32.6 -f values.taml