https://www.openpgp.org/software/kleopatra/
dnf install kleopatra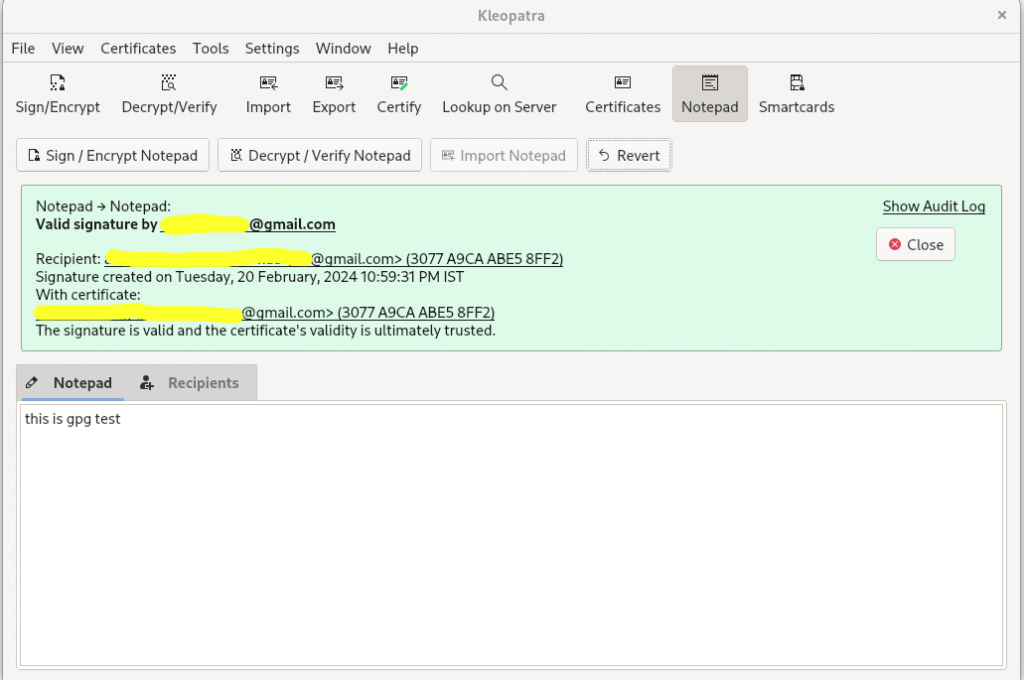
GCM is preferred over CBC
nmap --script ssl-enum-ciphers -p 443 example.comssl_ciphers HIGH:!aNULL:!MD5!TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256;Strip command strips the symbols form object file.
strip /path/to/binaryfile
strip -s /path/to/binaryfile
# on strip debug symbols
strip --strip-debug example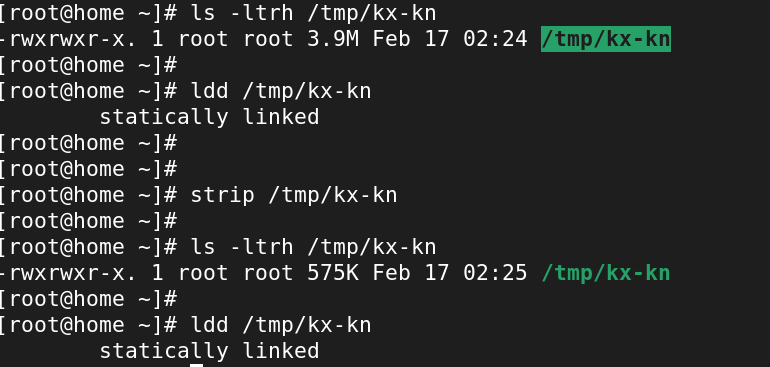
To view all symbols in binary(readelf)
readelf -s /path/to/binaryfilenm command:
nm /path/to/binaryfileMore
ad_join.sh
#!/bin/bash
#check if already joined to domain
if [[ $(realm list) != "" ]]
then
echo "This server is already joined to domain."
realm list | head -n 1
exit
fi
function update_sssd_config() {
sed -i 's/use_fully_qualified_names = True/use_fully_qualified_names = False/g' /etc/sssd/sssd.conf
sed -i 's|/home/%u@%d|/home/%u|g' /etc/sssd/sssd.conf
systemctl restart sssd
}
function restrict_ssh_access_group() {
if [[ $(cat /etc/ssh/sshd_config | grep -o "updated_by_ad_join") != "updated_by_ad_join" ]]
then
echo "###############updated_by_ad_join.sh###############" >> /etc/ssh/sshd_config
echo "AllowGroups root ssh-access-group" >> /etc/ssh/sshd_config
systemctl restart sshd
fi
}
function sudo_access_level_group() {
if [[ $(cat /etc/sudoers | grep -o "updated_by_ad_join") != "updated_by_ad_join" ]]
then
echo "###############updated_by_ad_join.sh###############" >> /etc/sudoers
echo "Cmnd_Alias SUDO_ACCESS_LEVEL1 = /usr/bin/ls, /usr/bin/cat " >> /etc/sudoers
echo "Cmnd_Alias SUDO_ACCESS_LEVEL2 = /usr/bin/vi, /usr/bin/nano " >> /etc/sudoers
echo "%sudo-group-level1 ALL=(ALL) NOPASSWD: SUDO_ACCESS_LEVEL1" >> /etc/sudoers
echo "%sudo-group-level2 ALL=(ALL) NOPASSWD: SUDO_ACCESS_LEVEL2" >> /etc/sudoers
echo "%sudo-group-full-access ALL=(ALL) NOPASSWD: ALL" >> /etc/sudoers
fi
}
#check os
if [[ $(cat /etc/os-release | egrep "centos|redhat|fedora|rhel|oracle|rocky") != "" ]]
then
yum install sssd realmd oddjob oddjob-mkhomedir adcli samba-common samba-common-tools krb5-workstation openldap-clients -y
realm join -vvv --user=administrator ad.example.com
#call function
update_sssd_config
restrict_ssh_access_group
sudo_access_level_group
fi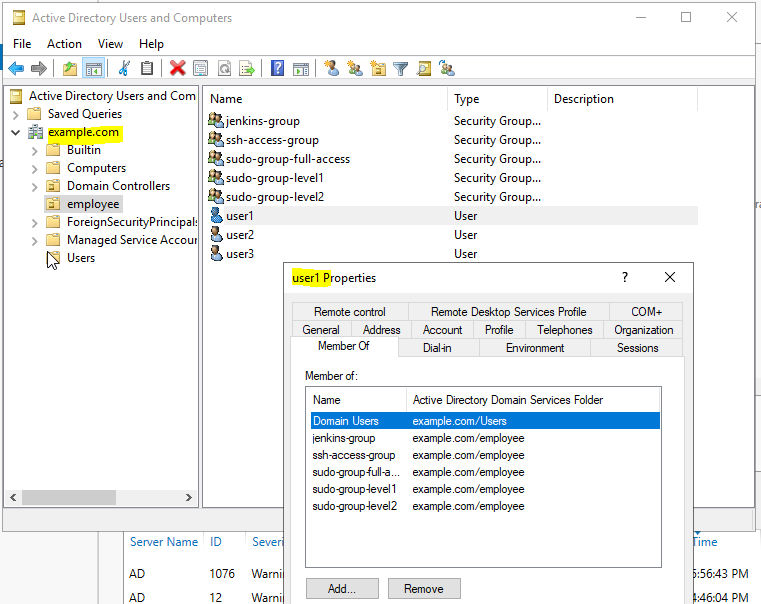
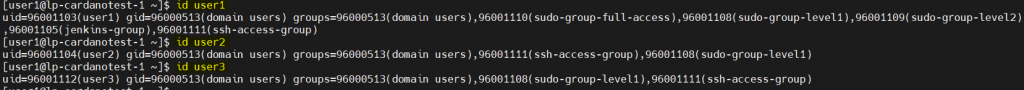
Method 1: (all user have same admin access)
Domain name : example.com
Domain Controller : ad.exmaple.com
Bind DN : jenkins-svc-account@example.com
Bind Password : <jenkins-svc-account password>
Else it will give Error: simple bind failed: ad.example.com:389 error
Also Domain Name(example.com) should be resolved from jenkins host or entry should be in /etc/hosts
192.168.122.6 example.com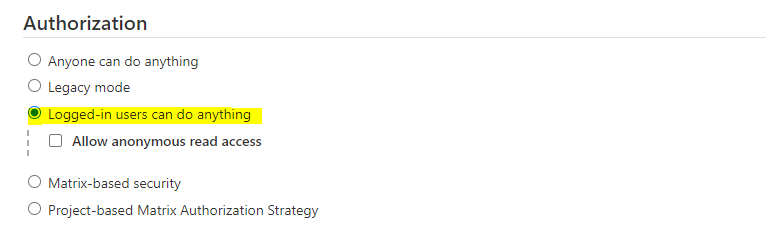
Method 2: Matrix-based security
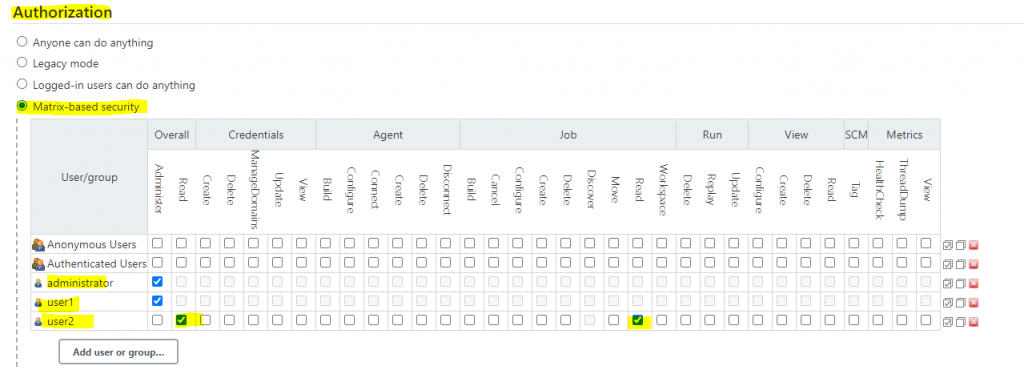
Method3: Role based strategy(pending)
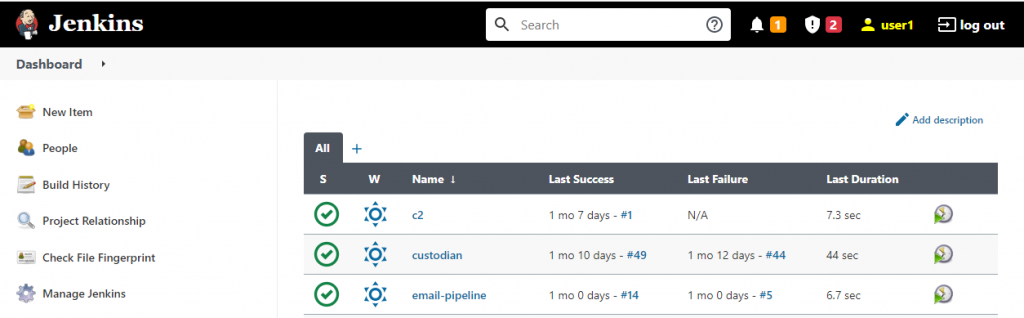
AD user and jenkins screenshot for reference
tnc example.com -port 389
Test-NetConnection -ComputerName example.com -Port 389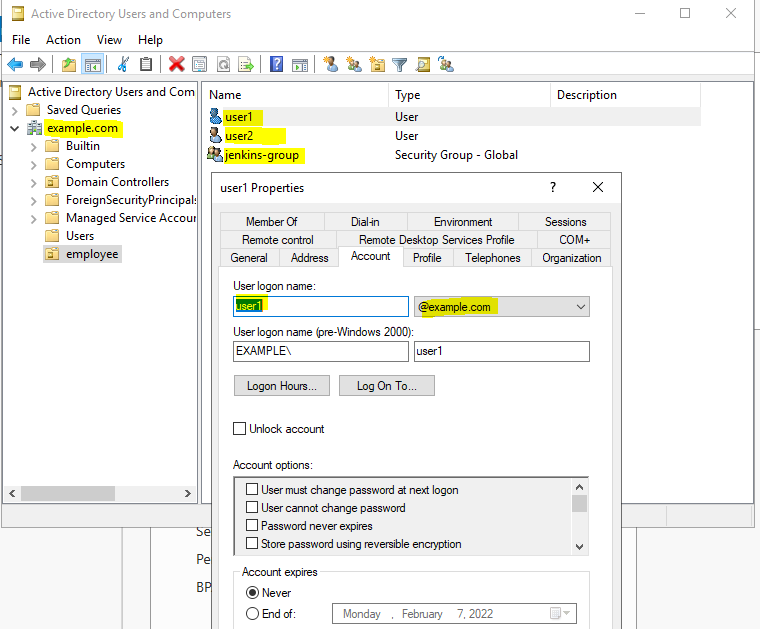
Why?
– Reduce surface attack
– Reduce docker image size
hola.sh
{-# LANGUAGE OverloadedStrings #-}
import Web.Scotty
import Data.Monoid (mconcat)
main = scotty 3000 $
get "/:word" $ do
beam <- param "word"
html $ mconcat ["<h1>Scotty, ", beam, " me up!</h1>"]alpine.Dockerfile
FROM haskell:8 AS build
WORKDIR /opt
RUN cabal update
RUN cabal install --lib scotty
COPY hola.hs .
#RUN ghc --make -threaded hola.hs -o hola
RUN ghc --make -threaded -optl-static -optl-pthread hola.hs -o hola
FROM alpine:3.15.0
RUN addgroup -S group1 && adduser -S user1 -G group1
USER user1
WORKDIR /opt
COPY --from=build /opt/hola .
EXPOSE 3000
CMD ["/opt/hola"]More on haskell static binary –
Docker
Jenkins
Kubernetes
Terraform
Ansible
General questions
AWS questions
Linux questions
Why?
– Optimize size
– less surface attack
FROM rust:slim-buster AS build
WORKDIR /opt
COPY . .
RUN rustup target add x86_64-unknown-linux-musl
RUN cargo build --target x86_64-unknown-linux-musl --release
FROM alpine:3.15.0
WORKDIR /opt
COPY --from=build /opt/target/x86_64-unknown-linux-musl/release .
EXPOSE 7878
CMD ["/opt/simple-rust-webserver"]docker build -t rust-web-alpine -f alpine.Dockerfile .
docker run -d -p 7878:7878 rust-web-alpine[root@lp-test-1 simple-rust-webserver]# docker images | grep rust-web-alpine
rust-web-alpine latest 7dd00663078c 9 minutes ago 9.4MBmain.rs
use std::net::{TcpStream, TcpListener};
use std::io::{Read, Write};
use std::thread;
fn handle_read(mut stream: &TcpStream) {
let mut buf = [0u8 ;4096];
match stream.read(&mut buf) {
Ok(_) => {
let req_str = String::from_utf8_lossy(&buf);
println!("{}", req_str);
},
Err(e) => println!("Unable to read stream: {}", e),
}
}
fn handle_write(mut stream: TcpStream) {
let response = b"HTTP/1.1 200 OK\r\nContent-Type: text/html; charset=UTF-8\r\n\r\n<html><body>hola rust</body></html>\r\n";
match stream.write(response) {
Ok(_) => println!("Response sent"),
Err(e) => println!("Failed sending response: {}", e),
}
}
fn handle_client(stream: TcpStream) {
handle_read(&stream);
handle_write(stream);
}
fn main() {
let listener = TcpListener::bind("0.0.0.0:7878").unwrap();
println!("Listening for connections on port {}", 7878);
for stream in listener.incoming() {
match stream {
Ok(stream) => {
thread::spawn(|| {
handle_client(stream)
});
}
Err(e) => {
println!("Unable to connect: {}", e);
}
}
}
}More : https://users.rust-lang.org/t/building-executable-for-alpine-linux/13568
#install clamav
yum -y install epel-release
yum install clamav
#update clamav
/usr/bin/freshclam
#scan clamav
clamscan -r /tmp/
more : https://www.hostinger.in/tutorials/how-to-install-clamav-centos7