docker run -v /tmp/zap:/zap/wrk -t owasp/zap2docker-stable zap-full-scan.py -t "https://api.photo.initedit.com" -g gen.conf -r "https://api.photo.initedit.com".htmlTag: security
falco runtime security
https://falco.org/docs/getting-started/installation/
rpm --import https://falco.org/repo/falcosecurity-3672BA8F.asc
curl -s -o /etc/yum.repos.d/falcosecurity.repo https://falco.org/repo/falcosecurity-rpm.repo
yum -y install falco
#load falco driver
falco-driver-loader
lsmod | grep falco
modprobe falco-probe
#run falco
falco
# adduser will show alert messageinstall openvas in centos8
sed -i 's/enforcing/disabled/g' /etc/selinux/config
reboot
dnf update
yum config-manager --set-enabled PowerTools
yum install epel-release
wget -q -O - http://www.atomicorp.com/installers/atomic |sh
yum install openvas
openvas-setupMore : https://github.com/Atomicorp/gvm
- Cronjob to update CVE database
10 1 * * * /usr/sbin/greenbone-nvt-sync > /dev/null
10 2 * * * /usr/sbin/greenbone-scapdata-sync > /dev/null
10 3 * * * /usr/sbin/greenbone-certdata-sync > /dev/nullOpenvas API:
gvm-cli --gmp-username USRENAME --gmp-password PASSWORD socket --sockpath /var/run/gvm/gvmd.sock --xml "<get_tasks/>"
gvm-cli socket --sockpath /var/run/gvm/gvmd.sock --xml "<get_version/>"Special File Permissions in linux setuid, setgid, sticky bit
setuid permission:
When program is executed with setuid permission it will executed as owner of that program.
-rwsr-xr-x. 1 root root 27856 Aug 9 2019 /usr/bin/passwdas passwd has setuid set that’s why normal user can reset their password
#exec will be as owner user
chmod u+s file_name
#exec will be as owner user
chmod 4750 file_name
setgid permission:
When program is executed with setgid permission it will executed as group owner of that program.
-r-xr-sr-x. 1 root tty 15344 Jun 10 2014 /usr/bin/wallas wall has setgid enabled it has all the permission as group tty has.
chmod u+g file_name
chmod 2700 file_nameSticky bit:
Owner of files and directory and root can only delete the file when sticky bit is set.
drwxrwxrwt. 16 root root 4096 Oct 10 10:10 tmp
all linux /tmp directory has sticky bit enabled.
chmod +t /tmpNOTE: Capital S,T displayed when user does not have execute permission on that file
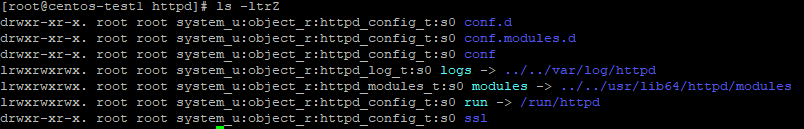
Apply selinux rules to file
Selinux add one more layer of security on top of linux.
To add SSL directory as per selinux context.
ls -ltrZ
sestatus -b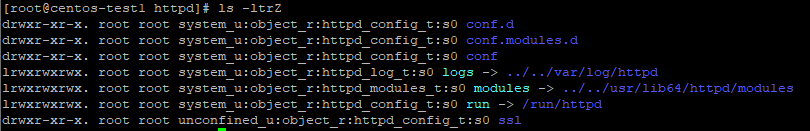
chcon -h system_u:object_r:httpd_config_t:s0 ssl