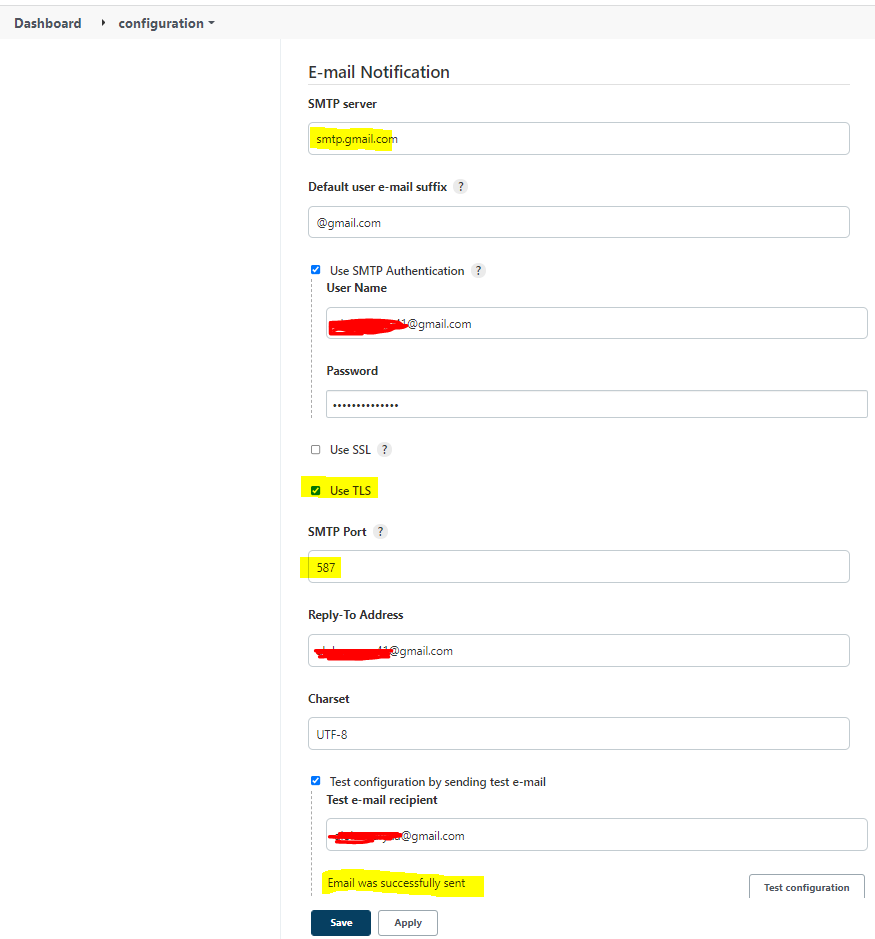
import smtplib
email_user = '<aws-ses-user>'
email_password = '<aws-ses-password>'
sent_from = '"test" <test@example.com>' #This should be verified
to = ['test2@example.com']
subject = 'test'
body = 'test'
email_text = """\
From: %s
To: %s
Subject: %s
%s
""" % (sent_from, ", ".join(to), subject, body)
try:
smtp_server = smtplib.SMTP_SSL('email-smtp.ap-south-1.amazonaws.com', 465)
smtp_server.ehlo()
smtp_server.login(email_user, email_password)
smtp_server.sendmail(sent_from, to, email_text)
smtp_server.close()
print ("Email sent successfully!")
except Exception as ex:
print ("Something went wrong….",ex)
Issues and error messages:
- Issues:
- https://serverfault.com/questions/639297/why-does-postfix-on-aws-give-me-invalid-mail-from-address-provided-i-have-pro/639300
- Something went wrong…. (501, b’Invalid MAIL FROM address provided’, ‘username’)
- Something went wrong…. (554, b’Message rejected: Email address is not verified. The following identities failed the check in region AP-SOUTH-1: test <test@example.com>, test@example.com’) – verify user in aws
- access key and smtp username is same
- get aws smtp password – https://docs.aws.amazon.com/ses/latest/DeveloperGuide/smtp-credentials.html